As an IT Director, I spend most of my time referencing information found inside the IT Service Management (ITSM) system and one of the better open source ITSM tools in the marketplace is GLPI. The feature set is massive and I’ve used this tool on and off for the last decade for IT inventory and helpdesk. On the security side, Single Sign On is paramount for authentication consistency and I tend to use SAML in most applications.
GLPI comes with several authentication options, including CAS, but it doesn’t include a way to authenticate users through SAML. As you may know, “Security Assertion Markup Language (SAML) is an open standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP).” (Varonis) In our case GLPI is the SAML service provider and any number of SAML identity providers (Azure AD, ADFS, Okta, One login, Google IdP) can be used to authenticate users.
The good news is that GLPI has a plugin API that can be used to augment the software with additional features. Having worked with GLPI previously on my Nagios Event Handlers project, I was ready to dig in and create the functionality. Using the API.
The plugin relies on OneLogin’s SAML PHP Toolkit, which is a PHP library that helps web developers create a SAML Service Provider in existing PHP software. The plugin stores the SAML configuration in the database and the software takes several inputs that I mapped to fields in the plugin setup.
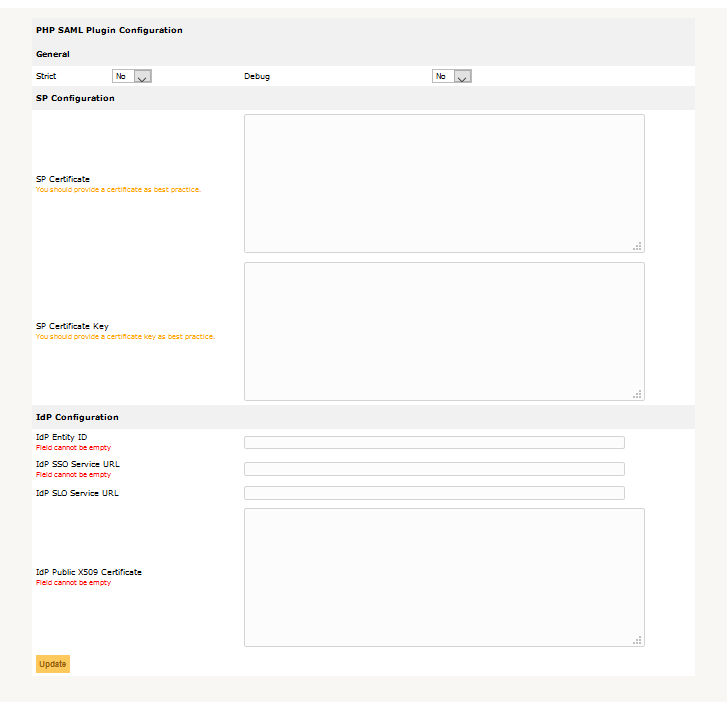
You can find the plugin at the GLPI Plugins website or at my repo on github. Please submit any bugs or feature requests to the github repo. If you found this plugin helpful, please leave a comment below.



Shigol
Hello!
Faced a problem. I installed the php-saml plugin on GLPI 10.0.3. Completed all fields on the configuration page. But when I try to get XML (/plugins/phpsaml/front/meta.php) for AD FS configuration, I get a blank page.
I use On-Premise AD FS.
Found out that there is no /php saml/lib/php-saml/settings.php file. If you create from settings_example.php, then meta.php starts displaying the information that is filled in this file. But ADFS won’t accept it…
The plugin is configurable in /php saml/lib/php-saml/settings.php not the plugin’s GUI?
marco
Hi,
Iam trying to integrate glpi SSO with keycloak. But i always get the following error VerificationException: SigAlg was null.
I am stuck on that. Can anyone help me please ?
Olivier Vigouroux
Hi Marco,
I try to install php_saml with keycloak. If you have succeed, could you explain how to configure realm, client, identity provider for plugin php_saml.
Thanks
HC Tan
Hi Derrick,
Once SSO had been activated on GLPI using your plugin, is there a way to still login with the local database default admin account that is not in AD?
Hope there’s a way…
Thanks.
Rajesh R
Hello Derrik, first of all, many thanks for this plugin
I really appreciated for a good plugin for glpi
Am trying to authenticate using google workspace account after that am receiving 403 app is not configured like that
Please help me in this issues.Waiting for your reply.
Manuel Johnen
This translation would be done by Google Translate and the original text is attached.
Hello Derrik, first of all, thank you very much for this plugin.
We have the challenge that the entries we have made are not saved.
Whenever you want to save the entries, you will be redirected to the GLPI start page and will then find an empty configuration page for the plugin.
Do you already have experience with such behavior and can you perhaps give the decisive tip why this could be?
Thanks for the support in advance.
Hallo Derrik, zunächst einmal vielen Dank für dieses Plugin.
Wir haben die Herausforderung, dass unsere getätigten Eingaben nicht gespeichert werden.
Immer wenn man die Eingaben speichern möchte, wird man zur Startseite von GLPI zurückgeleitet und findet anschließend eine leere Konfigurationsseite des Plugins.
Hast du bereits Erfahrung mit solch einem Verhalten und kannst vielleicht den entscheidenden Tipp geben, woran das liegen kann?
Danke für die Unterstützung im Voraus.
shane
just wondering what the metadata url would be
michael L
hi, thx for you script.
unfortunally, he did’nt work for me.
Details :
Webserver mutualised server, SSL “let’s encrypt”.
Azure P1
IN AAD :
Activate single auth SAML, put :
Entity ID : https://support.mywebsite.fr
assertion URL : https://support.mywebsite.fr/plugins/phpsaml/front/acs.php
Source attribut (name identifier) :
Email address : user.userprinpalname
Coping all the parameter into my gpli :
Connection url
AZURE AD ID
disconnect url
downloading my base64 certificat
IN GLPI :
open with blocnote, past to my glpi into x509 certificate
past the parameter login/disconnect/AAD ID
when i try to login, if i don’t put user or group, microsoft say NO, need one at less, so i do that.
When i try to login with an user (or a user un security group), the login page put me back to :
https://support.mywebsite.fr/plugins/phpsaml/front/acs.php and she is blank.
my first question :
did SP Certificate is absolutly necessary ?
Waiting for your answer.
greatfull.
Amritanshu
Hi,
I would like your assistance for configuring GLPI with SAML on KeyCloak SSO. I am able to access the redirect to SSO but always get “Invalid SAML Response” from GLPI.
Thanks!
Derrick
Difficult to know without seeing the logs or SAML trace. You can install the SAML Tracer extension in Firefox to obtain additional SAML logs. Also if you have set Strict to “Yes” then certificates must be fully validated.
Juan Cruz, Martinez Luquez
Hello Derrik, first of all, many thanks for this plugin.
I wonder if you can help me to configure it with Google SAML. Im the admin of both GLPI ans GSuite but I can not find de URL ACS and ID I must provide to Google.
Many thanks in advance.
Regards.
Derrick
The Entity ID will be your glpi base url. (e.g. glpi.yourdomain.com). The ACS url is {Your GLPI web server base URL}/plugins/phpsaml/front/acs.php
champaka
Hi Juan Cruz,
are you successfully configured Google sso? can you please help me to configure this?
Ricardo Campos Passanezi
Hello Derrik, I’m trying to use your plugin. And I have to apologize at first because of my ignorance: I turned the debug on but I cannot find where the debugs are being sent to.
Ou corporate account are Google (Oauth2 and SAML are available) but I’m not responsible for generating the IdP conf. I’ve received the info from the staff that takes care of it.
Anyway, thanks for the plugin. It’s very nice and will be very useful.
Ricardo.
Derrick
Debug sends errors to the php-error file in the GLPI logs folder.